Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap
Related Articles: Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap
Introduction
With great pleasure, we will explore the intriguing topic related to Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap
- 2 Introduction
- 3 Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap
- 3.1 The Importance of Apache Version Identification
- 3.2 Nmap Techniques for Apache Version Identification
- 3.3 FAQs Regarding Nmap Apache Version Identification
- 3.4 Tips for Effective Apache Version Identification with Nmap
- 3.5 Conclusion
- 4 Closure
Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap
![Find Network Vulnerabilities with Nmap Scripts [Tutorial] - YouTube](https://i.ytimg.com/vi/3U1pJ-eJrAU/maxresdefault.jpg)
In the ever-evolving landscape of cybersecurity, understanding the software powering websites is paramount. Apache, the world’s most popular web server, serves as the backbone for countless online platforms. However, its widespread use also presents a significant challenge: identifying specific Apache versions deployed across the internet. This knowledge is crucial for security professionals to assess potential vulnerabilities and implement appropriate mitigation strategies.
Enter Nmap, the ubiquitous network scanning tool, which provides valuable insights into the software running on remote systems. By leveraging Nmap’s capabilities, security researchers and practitioners can effectively identify Apache versions, paving the way for proactive security measures.
The Importance of Apache Version Identification
The significance of pinpointing Apache versions lies in their direct correlation with known vulnerabilities. Over time, security researchers uncover exploitable flaws within specific Apache versions. These vulnerabilities can range from minor inconveniences to severe security breaches, allowing attackers to gain unauthorized access, steal sensitive data, or disrupt website operations.
Identifying the Apache version running on a target system allows security professionals to:
- Assess Vulnerability Risk: By cross-referencing the detected Apache version with known vulnerability databases (e.g., CVE, NVD), security teams can determine the potential risks associated with the deployed software.
- Prioritize Patching Efforts: Knowing the specific Apache version enables organizations to prioritize patching efforts, focusing on addressing vulnerabilities that pose the most significant threats.
- Implement Targeted Security Controls: Understanding the Apache version empowers security teams to implement specific security controls, such as firewall rules, intrusion detection systems, and web application firewalls, tailored to the identified version.
- Conduct Effective Penetration Testing: Penetration testers can leverage Apache version information to tailor their attack vectors, simulating real-world scenarios and identifying exploitable weaknesses.
Nmap Techniques for Apache Version Identification
Nmap offers a versatile arsenal of techniques for Apache version detection. These methods range from passive fingerprinting to active probing, each providing unique advantages and limitations.
1. Passive Fingerprinting:
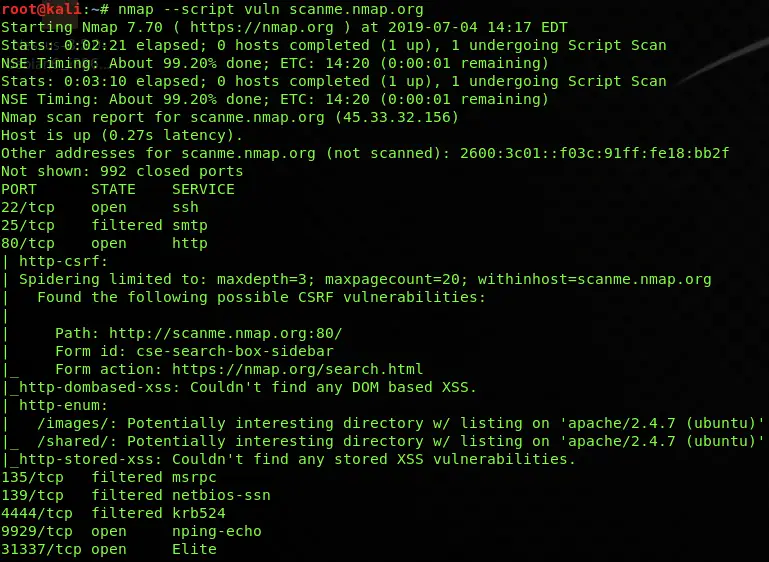
- Banner Grabbing: Nmap can passively identify the Apache version by analyzing the server’s response headers. This technique relies on the server’s default behavior, which often includes version information within the HTTP response. For example, a server might respond with "Server: Apache/2.4.54" in the header.
- HTTP Server Signature Analysis: Nmap can analyze the server’s response to specific HTTP requests, leveraging unique characteristics of different Apache versions. These signatures can include specific header values, response times, or error messages.
2. Active Probing:
- Version-Specific Port Scans: Nmap can scan for specific ports associated with known Apache versions. For example, certain versions may expose particular services or vulnerabilities on non-standard ports.
- Custom Scripting: Nmap allows users to write custom scripts that interact with the target server, probing for specific Apache version-related information. These scripts can be tailored to exploit unique vulnerabilities or identify specific configuration settings.
3. Combining Techniques:
- Multi-Stage Scans: Nmap can be used to combine passive and active techniques, providing a more comprehensive analysis. This approach leverages the strengths of each method, maximizing the chances of accurate version identification.
- Script Libraries: Nmap includes a vast library of scripts that can be used to automate Apache version identification. These scripts can perform various tasks, such as identifying common vulnerabilities or extracting specific configuration details.
FAQs Regarding Nmap Apache Version Identification
1. How accurate is Nmap in identifying Apache versions?
Nmap’s accuracy in identifying Apache versions depends on several factors, including:
- Server Configuration: If the server is configured to hide version information, Nmap’s ability to identify the version may be limited.
- Vulnerability Databases: The accuracy of Nmap’s results relies on the completeness and up-to-date nature of vulnerability databases.
- Nmap Script Library: The availability of appropriate scripts for specific Apache versions can influence the accuracy of the identification process.
2. Can Nmap identify all Apache versions?
Nmap cannot identify all Apache versions due to factors such as:
- Custom Configurations: Servers may be configured to hide version information or use custom headers, making identification challenging.
- Obscure Versions: Nmap’s script library may not include scripts for identifying obscure or rarely used Apache versions.
- Evolving Technology: As Apache evolves, new versions may emerge, requiring updates to Nmap’s script library.
3. What are the limitations of Nmap for Apache version identification?
Nmap’s limitations include:
- False Positives: Nmap may mistakenly identify a server as running a specific Apache version due to similarities in response patterns.
- False Negatives: Nmap may fail to identify the correct Apache version due to server configurations or incomplete vulnerability databases.
- Performance Considerations: Nmap scans can be resource-intensive, potentially impacting network performance or triggering security alerts.
4. How can I improve Nmap’s accuracy for Apache version identification?
To enhance Nmap’s accuracy, consider the following:
- Use a Comprehensive Script Library: Ensure that Nmap’s script library is up-to-date and includes scripts relevant to the Apache versions you are targeting.
- Configure Nmap for Maximum Information Gathering: Customize Nmap’s scan parameters to maximize information gathering, such as enabling banner grabbing, HTTP server signature analysis, and custom scripting.
- Validate Results with Other Tools: Use other security tools, such as web vulnerability scanners or security information and event management (SIEM) systems, to corroborate Nmap’s findings.
Tips for Effective Apache Version Identification with Nmap
- Use a Nmap Script Library: Leverage Nmap’s comprehensive script library, which includes scripts specifically designed for Apache version identification.
- Combine Passive and Active Techniques: Employ both passive fingerprinting and active probing to maximize the chances of accurate identification.
- Tailor Scans to Specific Needs: Customize Nmap scans to target specific Apache versions or vulnerabilities based on your security goals.
- Regularly Update Nmap and Scripts: Keep Nmap and its script library updated to ensure compatibility with the latest Apache versions and vulnerability databases.
- Integrate Nmap into Security Automation: Integrate Nmap into your existing security automation processes to streamline Apache version identification and vulnerability assessment.
Conclusion
Identifying Apache versions is a critical step in securing web applications and mitigating potential vulnerabilities. Nmap, with its diverse range of techniques and script library, provides a powerful tool for achieving this goal. By leveraging Nmap’s capabilities, security professionals can gain valuable insights into the software powering websites, enabling proactive security measures and mitigating the risks associated with exploitable flaws. As the internet landscape continues to evolve, the importance of tools like Nmap for understanding software versions and vulnerabilities will only grow, ensuring a more secure and resilient online environment.







Closure
Thus, we hope this article has provided valuable insights into Unmasking Web Server Vulnerabilities: Exploring Apache Version Identification with Nmap. We appreciate your attention to our article. See you in our next article!