Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing
Related Articles: Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing
- 2 Introduction
- 3 Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing
- 3.1 Understanding the Concept: Appending Random Data
- 3.2 Practical Applications: Unlocking the Potential of Data Manipulation
- 3.3 Implementing Random Data Manipulation with Nmap
- 3.4 FAQs: Addressing Common Concerns
- 3.5 Tips for Effective Data Manipulation: A Practical Guide
- 3.6 Conclusion: A Powerful Tool for Network Exploration and Security Auditing
- 4 Closure
Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing

Nmap, the Network Mapper, is a powerful tool used for network exploration and security auditing. While its primary function involves identifying and mapping network devices, its capabilities extend beyond basic discovery. Nmap offers a range of options for data manipulation, allowing users to modify packets sent and received during scans, thereby tailoring the scanning process to specific needs and objectives. One such technique involves appending random data to packets, a method that can significantly enhance the effectiveness of network discovery and security audits.
Understanding the Concept: Appending Random Data
Appending random data to packets involves adding a sequence of unpredictable bytes to the end of a packet before it is transmitted. This modification serves several purposes:
-
Stealth Mode: By adding random data, the scan becomes less predictable and harder to detect by intrusion detection systems (IDS) or firewalls that rely on signature-based detection. This makes the scan less likely to trigger alarms, allowing for a more discreet and stealthy approach.
-
Evasion Techniques: Appending random data can be used to evade certain types of security mechanisms that analyze packet content for specific patterns or signatures. By introducing randomness, the scan becomes less susceptible to these detection methods.
-
Network Fingerprinting: Appending random data can reveal information about a target’s network configuration and security posture. By observing how the target system responds to modified packets, security analysts can gain insights into the network’s security measures and potential vulnerabilities.
-
Enhanced Data Collection: Appending random data can be used to gather more comprehensive information about a network. By sending modified packets and analyzing the responses, security analysts can identify hidden services, detect unusual network behavior, and uncover potential security risks.
Practical Applications: Unlocking the Potential of Data Manipulation
The technique of appending random data finds its utility in various scenarios:
-
Network Discovery: By modifying packets, Nmap can identify devices that might otherwise remain hidden. This is particularly useful for detecting devices that use non-standard ports or employ obfuscation techniques to evade traditional scans.
-
Security Auditing: Appending random data can help uncover security weaknesses that might be overlooked by conventional scans. By testing a target’s response to modified packets, security analysts can identify vulnerabilities related to firewall rules, intrusion detection systems, and network segmentation.
-
Vulnerability Assessment: Appending random data can be used to test for specific vulnerabilities that might be triggered by certain packet modifications. This allows for a more targeted and efficient vulnerability assessment process.
-
Penetration Testing: In penetration testing scenarios, appending random data can be used to bypass security controls and gain unauthorized access to a network. This technique can be used to identify and exploit weaknesses in a target’s security posture.
Implementing Random Data Manipulation with Nmap
Nmap provides various options for appending random data to packets. The most common methods include:
-
–randomize-hosts: This option shuffles the order in which hosts are scanned, making it harder for intrusion detection systems to detect the scan.
-
–randomize-ports: This option randomizes the order in which ports are scanned, further obscuring the scan pattern.
-
–data-length: This option specifies the number of random bytes to append to each packet.
-
–data-payload: This option allows users to specify a custom payload to be appended to each packet.
These options can be combined to tailor the scan to specific needs and objectives. For instance, a security analyst might use a combination of --randomize-hosts, --randomize-ports, and --data-length to conduct a stealthy scan that avoids detection and gathers comprehensive network information.
FAQs: Addressing Common Concerns
Q: Is appending random data legal?
A: The legality of appending random data to packets depends on the specific context and applicable laws. In most cases, it is considered legal to send modified packets to devices within your own network or with the explicit consent of the network owner. However, it is essential to adhere to local laws and regulations regarding network security and data privacy.
Q: Can appending random data harm a network?
A: Appending random data, when used appropriately, should not harm a network. However, excessive or malicious use of this technique can lead to network instability or denial of service attacks. It is crucial to use this technique responsibly and only for legitimate purposes.
Q: How can I protect my network from scans that append random data?
A: Protecting your network from scans that append random data requires a multi-layered approach:
-
Firewall Rules: Implement strong firewall rules to block suspicious traffic and limit access to critical network resources.
-
Intrusion Detection Systems (IDS): Deploy IDS systems to detect and respond to anomalous network activity, including scans that modify packets.
-
Network Segmentation: Divide your network into smaller segments to limit the impact of attacks and prevent attackers from spreading laterally.
-
Security Awareness Training: Educate users about the risks associated with network security and encourage them to report suspicious activity.
Q: Does appending random data guarantee anonymity?
A: Appending random data can make a scan less detectable, but it does not guarantee anonymity. Skilled security analysts can still identify and analyze the scan traffic, even with modified packets. To achieve true anonymity, more advanced techniques like VPNs or Tor networks are required.
Tips for Effective Data Manipulation: A Practical Guide
-
Start with small payloads: Begin with small amounts of random data and gradually increase the payload size as needed.
-
Monitor the network: Keep a close eye on the network during and after the scan to ensure that the modifications do not cause any adverse effects.
-
Document your actions: Maintain detailed records of all modifications made to packets, including the purpose, date, and time of the scan.
-
Be mindful of legal and ethical considerations: Always adhere to local laws and regulations regarding network security and data privacy.
-
Use specialized tools: Consider using specialized tools designed for network analysis and security auditing, such as Wireshark, to analyze the scan traffic and identify potential security issues.
Conclusion: A Powerful Tool for Network Exploration and Security Auditing
Appending random data to packets is a powerful technique that can significantly enhance the effectiveness of network discovery and security auditing. By modifying packets, security analysts can gain deeper insights into network configurations, identify hidden devices, and uncover potential vulnerabilities that might otherwise remain undetected. However, it is crucial to use this technique responsibly and ethically, adhering to local laws and regulations and considering the potential impact on the network. By leveraging Nmap’s data manipulation capabilities, security professionals can conduct more effective and comprehensive network assessments, ultimately strengthening the security posture of their organizations.



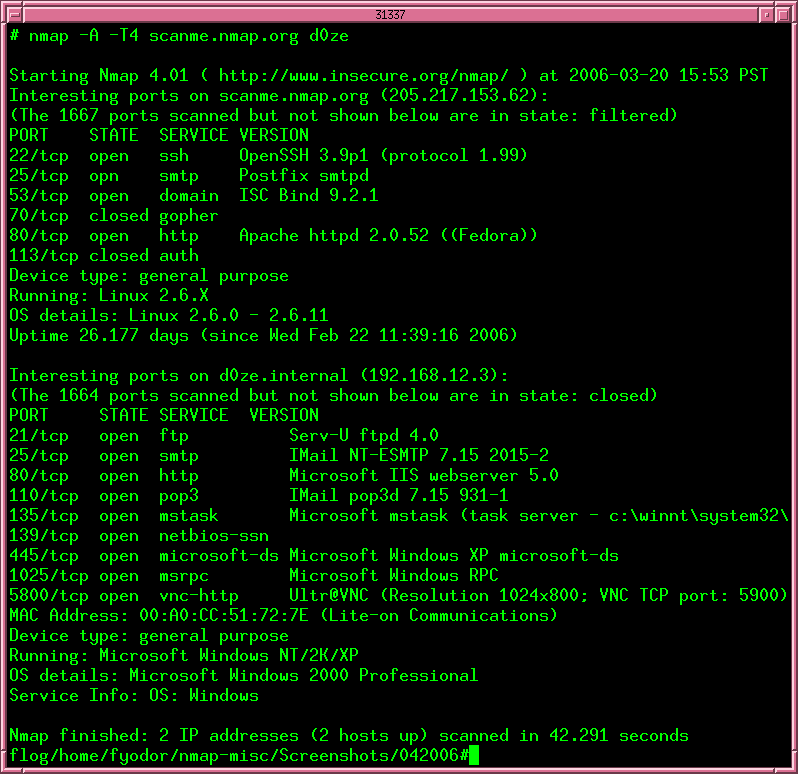



Closure
Thus, we hope this article has provided valuable insights into Nmap’s Data Manipulation: Enhancing Network Discovery and Security Auditing. We hope you find this article informative and beneficial. See you in our next article!