Nmap: The Essential Tool for Network Exploration and Security Auditing
Related Articles: Nmap: The Essential Tool for Network Exploration and Security Auditing
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Nmap: The Essential Tool for Network Exploration and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap: The Essential Tool for Network Exploration and Security Auditing

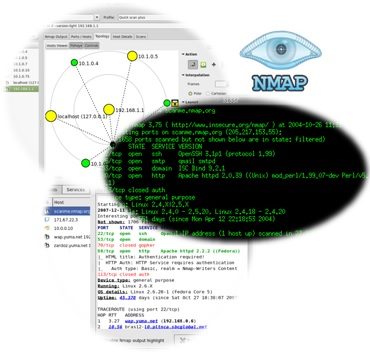
Nmap, short for Network Mapper, is a powerful and versatile open-source tool used for network discovery, security auditing, and vulnerability scanning. Its ability to scan networks and identify active hosts, services, and vulnerabilities has made it an indispensable tool for network administrators, security professionals, and researchers alike. This article provides a comprehensive overview of Nmap, exploring its capabilities, usage, and benefits in detail.
Understanding Nmap’s Core Functions
Nmap’s primary function is to send specially crafted network packets to target systems and analyze the responses received. This process, known as network scanning, allows Nmap to gather information about the network infrastructure, including:
- Host Discovery: Nmap can identify active hosts on a network by sending probes and detecting responses. This process helps determine which machines are online and accessible.
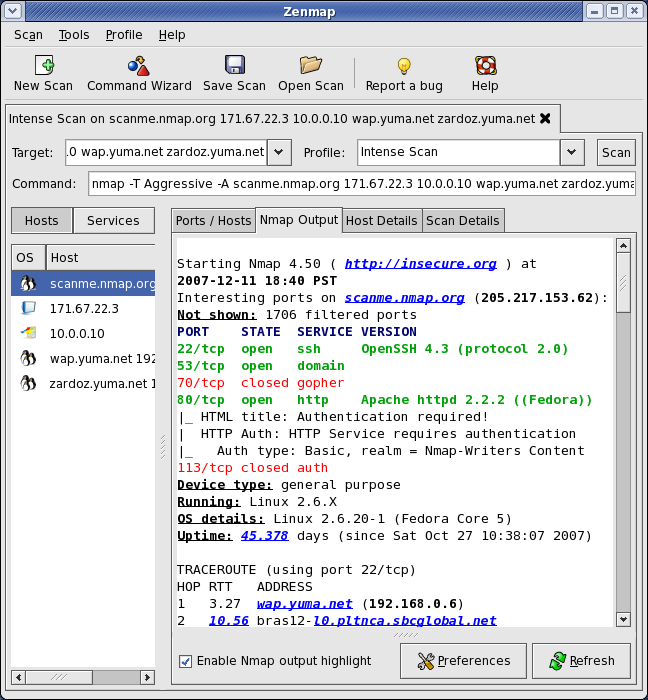
- Service Detection: Nmap identifies the services running on discovered hosts, including their ports, protocols, and versions. This information reveals potential security vulnerabilities and allows for targeted analysis.
- Operating System (OS) Detection: Nmap can often identify the operating system running on a target host based on the responses it receives. This is crucial for tailoring security assessments and exploiting known vulnerabilities specific to particular operating systems.
- Network Mapping: Nmap can generate graphical visualizations of network topologies, illustrating the connections between devices and the flow of data. This aids in understanding network structure and identifying potential bottlenecks or security risks.
- Vulnerability Scanning: Nmap can identify known security vulnerabilities on target systems by probing for specific weaknesses and exploiting them. This allows for proactive security assessments and the identification of potential attack vectors.
Nmap’s Versatility: A Toolkit for Diverse Applications
Nmap’s versatility stems from its diverse scanning techniques and a wide range of options for customizing scans. These capabilities enable it to be used for a broad spectrum of tasks, including:
- Network Security Auditing: Nmap is a core tool for security professionals to identify vulnerabilities, misconfigurations, and potential attack surfaces. It assists in implementing proactive security measures and detecting unauthorized access points.
- Network Inventory Management: Nmap helps network administrators maintain an accurate inventory of devices on the network, including their hardware and software specifications. This facilitates efficient management and troubleshooting.
- Penetration Testing: Nmap is widely used in penetration testing to simulate real-world attacks and identify exploitable vulnerabilities before malicious actors can exploit them.
- Network Troubleshooting: Nmap aids in diagnosing network connectivity issues by identifying network devices, their status, and potential bottlenecks.
- Research and Development: Nmap is a valuable tool for researchers studying network security, network performance, and emerging technologies. Its ability to gather detailed network information provides valuable insights for analysis and experimentation.
Delving Deeper into Nmap’s Capabilities
Nmap offers a comprehensive set of features that enhance its effectiveness and allow for tailored scans:
- Scanning Techniques: Nmap employs various scanning techniques, including SYN scans, UDP scans, and ACK scans, each tailored to specific purposes and network environments.
- Script Engine: Nmap’s script engine allows users to run custom scripts during scans to automate specific tasks, such as identifying specific services or vulnerabilities.
- Output Formats: Nmap supports various output formats, including text, XML, and HTML, facilitating data analysis and report generation.
- Advanced Options: Nmap provides numerous advanced options for customizing scans, such as setting timeouts, specifying port ranges, and using proxies.
- Integration with Other Tools: Nmap seamlessly integrates with other security tools, such as Metasploit and Wireshark, for comprehensive security assessments.
Navigating Nmap’s Command-Line Interface
Nmap’s primary interface is a command-line interface (CLI). While initially daunting for beginners, the CLI offers a powerful and flexible way to control Nmap’s behavior. Its syntax is consistent and logical, making it easier to learn and master with practice.
Common Nmap Commands and Examples:
-
Basic Host Discovery:
nmap -sn 192.168.1.0/24– This command performs a simple ping scan to identify active hosts within the 192.168.1.0/24 network. -
Port Scanning:
nmap -p 80,443 192.168.1.1– This command scans ports 80 and 443 on the target host 192.168.1.1. -
Operating System Detection:
nmap -O 192.168.1.1– This command attempts to identify the operating system running on the target host. -
Version Scanning:
nmap -sV 192.168.1.1– This command attempts to determine the versions of services running on the target host. -
Vulnerability Scanning:
nmap -sC 192.168.1.1– This command runs default Nmap scripts to identify potential vulnerabilities.
Frequently Asked Questions (FAQs) about Nmap
1. Is Nmap Legal to Use?
Nmap is a legitimate tool and its use is generally legal. However, it is crucial to understand and comply with local laws and regulations regarding network scanning. In particular, it is essential to obtain proper authorization before scanning networks that are not your own.
2. Is Nmap Suitable for Beginners?
Nmap can be initially challenging for beginners due to its command-line interface. However, numerous resources, including tutorials, documentation, and online communities, are available to help users learn and master Nmap.
3. How Can I Prevent My Network from Being Scanned by Nmap?
While completely preventing Nmap scans is difficult, implementing security measures such as firewalls, intrusion detection systems, and network segmentation can significantly reduce the effectiveness of Nmap scans.
4. What are the Best Practices for Using Nmap?
- Obtain Permission: Always obtain permission before scanning networks that are not your own.
- Minimize Scan Impact: Use appropriate scanning techniques and options to minimize the impact on network performance.
- Respect Privacy: Avoid scanning private networks or systems without proper authorization.
- Stay Updated: Regularly update Nmap to benefit from new features and security patches.
Tips for Effective Nmap Usage
- Start with Basic Scans: Begin with simple scans to understand Nmap’s output and gradually explore more advanced features.
- Utilize Script Engine: Leverage Nmap’s script engine to automate tasks and customize scans for specific purposes.
- Experiment with Options: Explore Nmap’s numerous options to tailor scans to your specific needs.
- Document Your Findings: Carefully document your scan results to facilitate analysis and reporting.
- Stay Informed: Stay updated on the latest Nmap features, security vulnerabilities, and best practices.
Conclusion
Nmap is a powerful and versatile tool that has become an essential resource for network professionals, security researchers, and anyone seeking to gain deeper insights into network infrastructure. Its ability to identify active hosts, services, and vulnerabilities makes it an invaluable tool for network security auditing, penetration testing, and network management. By mastering Nmap’s capabilities, users can enhance their network security posture, identify potential threats, and ensure the stability and integrity of their networks.




Closure
Thus, we hope this article has provided valuable insights into Nmap: The Essential Tool for Network Exploration and Security Auditing. We hope you find this article informative and beneficial. See you in our next article!