Nmap and the Power of Data Manipulation: A Comprehensive Guide
Related Articles: Nmap and the Power of Data Manipulation: A Comprehensive Guide
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap and the Power of Data Manipulation: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap and the Power of Data Manipulation: A Comprehensive Guide

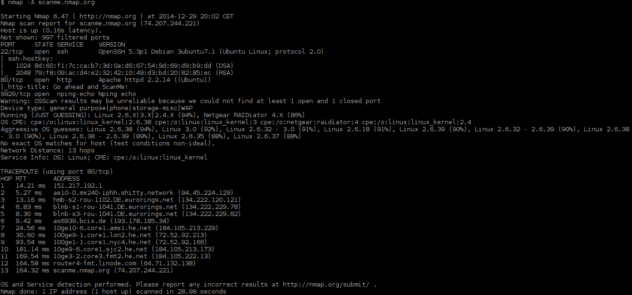
Nmap, the Network Mapper, is a widely used and powerful tool for network exploration and security auditing. Its versatility extends beyond simple port scanning, allowing for intricate manipulation of data packets. This capability, often referred to as "data appending," empowers users to inject custom information into network traffic, opening up a range of possibilities for network analysis, security testing, and even application-specific interactions.
Understanding Data Appending
At its core, data appending involves modifying the content of network packets before they are transmitted. This modification can range from simple alterations like adding a few bytes of data to crafting complex payloads designed to trigger specific responses from target systems. This ability to manipulate data flows directly impacts the way Nmap interacts with the network, enhancing its capabilities and offering new avenues for exploration.
Applications of Data Appending
The ability to append arbitrary data to network packets unlocks a diverse set of applications, ranging from network analysis to security testing and beyond. Here’s a breakdown of some prominent use cases:
1. Network Analysis and Troubleshooting:
- Protocol Analysis: By injecting specific data payloads, users can trigger responses from target systems, revealing detailed information about the protocols they implement and their underlying behavior. This allows for in-depth network analysis and troubleshooting, identifying potential issues and vulnerabilities.
- Network Mapping: Data appending can be used to identify hidden devices or services on a network. By crafting custom packets that trigger responses from otherwise silent devices, users can gain a more comprehensive understanding of the network’s topology.
- Service Discovery: Nmap’s data appending capabilities can be used to discover specific services running on a network. By sending carefully crafted packets to target ports, users can elicit responses that reveal the services running on those ports, even if they are not traditionally advertised.
2. Security Testing and Vulnerability Assessment:
- Vulnerability Scanning: Data appending allows for customized vulnerability scanning. By injecting crafted payloads designed to exploit specific vulnerabilities, users can identify potential security weaknesses in target systems. This provides a more targeted and effective approach to vulnerability assessment.
- Fuzzing: Data appending is crucial for fuzzing, a technique used to identify vulnerabilities by sending random or malformed data to target systems. By manipulating the data sent to applications, users can test the system’s resilience to unexpected inputs and uncover potential security flaws.
- Penetration Testing: Data appending plays a critical role in penetration testing. By crafting custom payloads designed to bypass security controls, attackers can gain unauthorized access to target systems. This allows for a realistic assessment of the system’s security posture.
3. Application-Specific Interactions:
- Protocol Exploitation: Data appending can be used to exploit vulnerabilities in specific protocols. By crafting custom packets that trigger specific responses from target systems, users can gain unauthorized access or manipulate the system’s behavior.
- Network Automation: Data appending can be used to automate network tasks. By crafting custom packets that control specific devices, users can automate tasks such as device configuration, network management, and data transfer.
- Custom Scripting: Nmap’s scripting capabilities allow users to craft custom scripts that leverage data appending for unique interactions with network devices and applications. This allows for targeted network analysis and automation tailored to specific needs.
Understanding the Mechanics of Data Appending
Nmap’s data appending capabilities are implemented through its powerful scripting engine, which allows users to define custom scripts that manipulate network packets. These scripts, written in a Lua-based language, provide a flexible framework for crafting custom data payloads and interacting with network traffic.
Key Features of Nmap’s Scripting Engine:
- Packet Manipulation: Scripts can modify the content of network packets, including headers and payloads, allowing for fine-grained control over the data being sent.
- Data Encoding and Decoding: Scripts can encode and decode data using various formats, enabling the manipulation of complex data structures and protocols.
- Network Interaction: Scripts can interact with the network, sending and receiving packets, analyzing responses, and performing actions based on the received data.
- Custom Logic: Scripts can implement custom logic, allowing users to define specific actions and responses based on the network conditions.
Examples of Data Appending in Action
To illustrate the practical applications of data appending, consider these examples:
- Identifying Hidden Services: A script could be crafted to send custom packets to a specific port, designed to trigger a response from a hidden service. The response, if received, would reveal the existence of the service and its associated information.
- Testing for SQL Injection Vulnerabilities: A script could be designed to inject malicious SQL queries into web applications, attempting to exploit SQL injection vulnerabilities. The script would analyze the response from the web server, identifying potential vulnerabilities based on the returned data.
- Automating Network Device Configuration: A script could be written to send custom configuration commands to network devices, automating tasks such as setting up network settings, managing user accounts, and updating firmware.
FAQs about Nmap Data Appending
1. Is data appending only for advanced users?
While scripting requires some technical expertise, Nmap provides a range of pre-built scripts that simplify data appending for various tasks. Users can leverage these scripts without needing to write their own, making data appending accessible even to those with limited scripting experience.
2. Can data appending be used for malicious purposes?
Yes, data appending can be misused for malicious activities, such as exploiting vulnerabilities, gaining unauthorized access, or launching denial-of-service attacks. It is crucial to use this capability responsibly and ethically, respecting the security and privacy of target systems.
3. Is data appending legal?
The legality of data appending depends on the specific context and the intended purpose. Using it for security testing or network analysis is generally considered acceptable, but using it for malicious purposes is illegal and can have serious consequences.
Tips for Using Nmap Data Appending Effectively
- Understand the Target System: Before using data appending, thoroughly research the target system and its protocols to ensure you are sending appropriate data payloads.
- Start with Pre-Built Scripts: Leverage Nmap’s pre-built scripts to familiarize yourself with data appending and its applications.
- Learn Scripting: Invest time in learning Nmap’s scripting language to craft custom scripts tailored to your specific needs.
- Be Ethical and Responsible: Use data appending responsibly and ethically, respecting the security and privacy of target systems.
Conclusion
Nmap’s data appending capabilities offer a powerful tool for network exploration, security testing, and application-specific interactions. By manipulating network packets and crafting custom payloads, users can gain deeper insights into network behavior, identify vulnerabilities, and automate network tasks. While this capability can be misused, responsible and ethical use of data appending can significantly enhance network security and analysis. Mastering Nmap’s scripting engine and leveraging its pre-built scripts empowers users to harness the full potential of data appending, unlocking new possibilities for network exploration and manipulation.




Closure
Thus, we hope this article has provided valuable insights into Nmap and the Power of Data Manipulation: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!