Navigating the Digital Landscape: A Comprehensive Guide to VPN-Enabled Network Drive Mapping
Related Articles: Navigating the Digital Landscape: A Comprehensive Guide to VPN-Enabled Network Drive Mapping
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Digital Landscape: A Comprehensive Guide to VPN-Enabled Network Drive Mapping. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Digital Landscape: A Comprehensive Guide to VPN-Enabled Network Drive Mapping
In the contemporary digital landscape, where data security and remote access are paramount, the ability to seamlessly connect to and manage remote network drives has become increasingly crucial. Traditional methods of accessing files stored on remote servers often present security vulnerabilities and logistical challenges, particularly in environments where data confidentiality and user authentication are critical. Enter VPN-enabled network drive mapping applications – innovative tools that bridge the gap between local and remote data storage, offering a secure and efficient way to access and manage files from anywhere in the world.
Understanding the Concept: VPN-Enabled Network Drive Mapping
At its core, VPN-enabled network drive mapping leverages the power of Virtual Private Networks (VPNs) to establish secure, encrypted connections between a user’s device and a remote server. This encrypted connection acts as a virtual tunnel, shielding data transmissions from prying eyes and ensuring data integrity. By mapping network drives through this secure tunnel, users can access and manage files stored on remote servers as if they were directly connected, eliminating the need for complex file sharing protocols or risky public network access.
Benefits of VPN-Enabled Network Drive Mapping
The advantages of employing VPN-enabled network drive mapping extend beyond enhanced security and seamless remote access. Here are some key benefits:
-
Enhanced Security: VPNs encrypt all data transmitted between the user’s device and the remote server, making it virtually impossible for unauthorized individuals to intercept or access sensitive information. This is especially critical for businesses handling confidential data, intellectual property, or customer information.
-
Improved Remote Access: VPN-enabled network drive mapping provides users with a convenient and secure way to access and manage files stored on remote servers, regardless of their physical location. This is invaluable for remote workers, traveling professionals, or anyone needing to access data from multiple locations.
-
Simplified File Management: By mapping remote drives to their local systems, users can manage files stored on remote servers with the same ease and familiarity as they would local files. This simplifies file organization, collaboration, and data sharing, streamlining workflows and improving productivity.
-
Centralized Data Storage: VPN-enabled network drive mapping facilitates centralized data storage, ensuring all files are accessible from a single location. This simplifies data backup and recovery procedures, minimizing downtime and potential data loss.
-
Increased Collaboration: By providing secure access to shared network drives, VPN-enabled solutions facilitate collaboration among team members, regardless of their physical locations. This fosters seamless data sharing and teamwork, enhancing productivity and project efficiency.
Key Features of VPN-Enabled Network Drive Mapping Applications
Modern VPN-enabled network drive mapping applications offer a diverse range of features designed to enhance security, user experience, and overall functionality. Some key features include:
-
Secure Connection Protocols: Robust encryption algorithms, such as AES-256, ensure data confidentiality and integrity throughout the connection.
-
Authentication Mechanisms: Secure user authentication methods, such as two-factor authentication, prevent unauthorized access and maintain data security.
-
Automatic Connection Management: Applications can automatically establish and maintain VPN connections, ensuring seamless access to remote drives without requiring manual intervention.
-
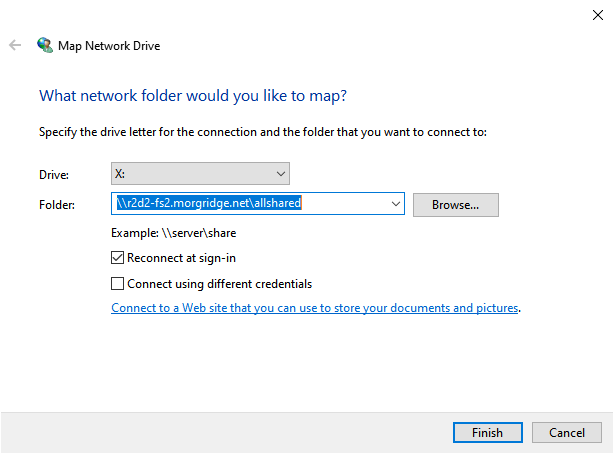
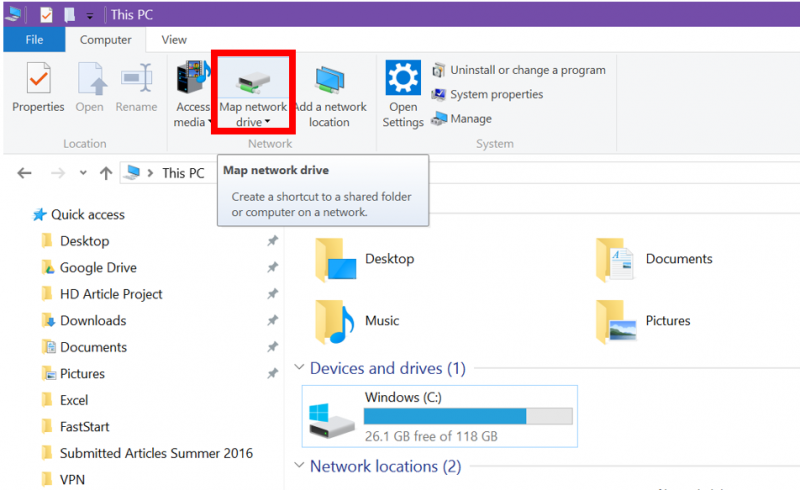
Drive Mapping Capabilities: These applications enable users to map multiple network drives to their local systems, providing a unified view of all their files and folders.
-
File Synchronization: Some applications offer file synchronization features, automatically updating local copies with any changes made on the remote server, ensuring data consistency across all devices.
-
Data Backup and Recovery: Integrated data backup and recovery functionalities ensure data integrity and minimize downtime in case of unexpected events or system failures.
-
User-Friendly Interface: Intuitive and user-friendly interfaces simplify the process of connecting to remote drives, mapping them to local systems, and managing files.
Applications of VPN-Enabled Network Drive Mapping
The versatility of VPN-enabled network drive mapping makes it an invaluable tool across various sectors and industries. Here are some prominent applications:
-
Business and Enterprise: Businesses utilize these applications for secure remote access to company servers, allowing employees to access critical data and applications from anywhere, enhancing productivity and collaboration.
-
Education: Educational institutions utilize VPN-enabled network drive mapping to provide students and faculty secure access to shared resources, facilitating collaborative projects and research.
-
Healthcare: Healthcare organizations leverage these applications for secure access to patient records, medical images, and other sensitive data, ensuring confidentiality and compliance with HIPAA regulations.
-
Government and Public Sector: Government agencies and public sector organizations utilize VPN-enabled network drive mapping for secure data access and collaboration, ensuring the protection of sensitive information and compliance with regulations.
Implementation Considerations
While VPN-enabled network drive mapping offers numerous benefits, successful implementation requires careful planning and consideration. Here are some key factors to consider:
-
Security Protocols: Choose an application that utilizes robust encryption protocols and strong authentication mechanisms to ensure data security.
-
Network Infrastructure: Ensure your network infrastructure is capable of supporting VPN connections and secure data transfer.
-
User Authentication: Implement secure user authentication methods, such as multi-factor authentication, to prevent unauthorized access.
-
Data Backup and Recovery: Establish robust data backup and recovery procedures to minimize data loss in case of system failures or unexpected events.
-
Compliance with Regulations: Ensure your chosen application complies with relevant data privacy and security regulations, such as GDPR or HIPAA.
FAQs on VPN-Enabled Network Drive Mapping
Q: Is it safe to use VPN-enabled network drive mapping?
A: Yes, VPN-enabled network drive mapping is generally safe when implemented correctly. By utilizing strong encryption protocols and secure authentication mechanisms, these applications provide a secure and reliable way to access and manage remote files. However, it is crucial to choose a reputable application provider and implement robust security measures to mitigate any potential risks.
Q: What are the potential risks of using VPN-enabled network drive mapping?
A: Potential risks associated with VPN-enabled network drive mapping include:
-
Data Breaches: Despite strong encryption, data breaches can occur if the VPN provider’s security is compromised or if the user falls victim to phishing attacks.
-
VPN Provider Reliability: The reliability of the VPN provider is crucial for uninterrupted access to remote drives. Choose a reputable provider with a proven track record of security and uptime.
-
User Error: Improper configuration or misuse of the application can lead to security vulnerabilities or data loss.
Q: How can I ensure the security of my VPN-enabled network drive mapping solution?
A: To ensure security, consider the following:
-
Choose a reputable VPN provider: Opt for a provider with a strong security track record and robust encryption protocols.
-
Enable strong authentication: Utilize two-factor authentication or other multi-factor authentication methods to prevent unauthorized access.
-
Keep your software updated: Regularly update your VPN software and operating system to patch security vulnerabilities.
-
Use a strong password: Choose a strong, unique password for your VPN account and avoid reusing it for other online services.
-
Be cautious of phishing attacks: Be wary of suspicious emails or links that request your VPN credentials or other sensitive information.
Tips for Using VPN-Enabled Network Drive Mapping
-
Choose a reputable application provider: Research different providers and select one with a strong reputation for security and reliability.
-
Configure the application correctly: Follow the provider’s instructions carefully and ensure the application is properly configured for optimal security and performance.
-
Use strong passwords: Choose unique, strong passwords for your VPN account and other online services.
-
Keep your software updated: Regularly update your VPN software and operating system to patch security vulnerabilities.
-
Be aware of potential risks: Understand the potential risks associated with VPN-enabled network drive mapping and implement appropriate security measures to mitigate them.
Conclusion
VPN-enabled network drive mapping has emerged as a vital tool for organizations and individuals seeking secure and efficient access to remote data. By leveraging the power of VPN technology, these applications provide a secure, encrypted connection between users and remote servers, enabling seamless file management, enhanced collaboration, and improved data security.
However, successful implementation requires careful planning, consideration of security protocols, and a commitment to best practices. By adhering to recommended security measures and choosing reputable application providers, users can harness the full potential of VPN-enabled network drive mapping to navigate the digital landscape with confidence and security.



Closure
Thus, we hope this article has provided valuable insights into Navigating the Digital Landscape: A Comprehensive Guide to VPN-Enabled Network Drive Mapping. We hope you find this article informative and beneficial. See you in our next article!